Any business that has an IT infrastructure should consider having penetration tests so that all vulnerabilities are safely exploited by white hackers who will help you re-evaluate your IT security. As flawless as you may consider your operating systems, networks, services and applications, there are flaws, and there are cybercriminals looking to take advantage of them for personal gain. The assessments based on penetration testing are useful for validating the state of your defensive mechanism, and the end-user adherence to your business’ security policies.
A penetration test is usually performed using automated or manual technologies to systematically compromise wireless networks, network devices, servers, web applications, endpoints, mobile devices and other points of exposure. Once vulnerabilities have been exploited in a particular system, the pen-testers may try to use the system to launch more exploits at other internal resources. Once they get into your system, they can incrementally try to achieve higher levels of clearance and deeper access to electronic information.
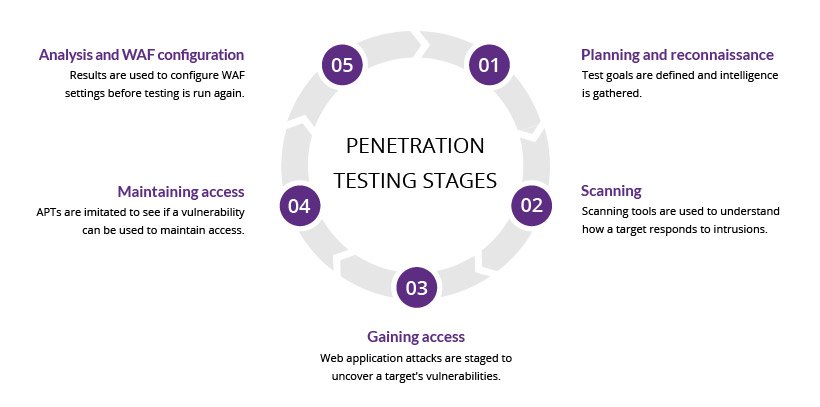
That being said, a penetration test can provide the network system and IT managers with essential information so that they can come up with a strategic conclusion and prioritise related recovery, remediation, and prevention methods. Simply put, the entire purpose of this testing is to evaluate the feasibility of end-user or system compromises and evaluate the related consequences that these incidents can have on the business’ operations or resources.
Penetration testers are typically outsourced, and not only do they test your IT infrastructure, they oftentimes use social engineering to exploit human error and negligence. That being said, penetration testing should be done regularly to meet regulatory requirements and avoid liability, preserve customer loyalty and corporate image, avoid costs of network downtime, ensure business continuity and help you intelligently manage vulnerabilities.
Generally, the penetration testers will reveal how emerging vulnerabilities and discovered threats may be assailed by cybercriminals. Besides performing regularly scheduled assessments and analysis, tests can also be run whenever new office locations are established, end-user policies are modified, security patches are applied, big modifications or upgrades are applied to applications or infrastructure, and when new applications or network infrastructure is added.
That being said, every business with an IT presence should highly consider hiring pen-testers to check for vulnerabilities, so that all the valuable data and assets can be properly protected. This is especially important for businesses that deal with sensitive information since there are very strict rules and regulations about safeguarding sensitive client data.



